Guarding Your Digital Fortress: The Importance of Social Media Privacy in Today's Interconnected World
In an era where our digital footprints often speak louder than our words, social media privacy isn't just a setting—it's your armor, your strategy, and, increasingly, your lifeline. Understanding and implementing robust privacy measures has become crucial for individuals and businesses as we navigate the complex web of online interactions. Let's dive deep into why it matters and how you can become the ultimate guardian of your digital realm.
The Great Data Heist: A Cautionary Tale for the Ages
Picture this: It's 2018, and the digital world is rocked by a scandal that would make even the most seasoned cybersecurity experts gasp. Cambridge Analytica, a name that would soon become synonymous with data misuse, is caught harvesting the personal data of millions of Facebook users without their consent.
The fallout was nuclear: Facebook, the social media giant once thought invincible, is slapped with a staggering $5 billion fine by the U.S. Federal Trade Commission. Cambridge Analytica, unable to weather the storm of global outrage, files for bankruptcy. But the real casualties? The millions of users whose trust was betrayed and whose personal information was exploited for political gain.
This wasn't just a wake-up call; it was a blaring alarm that echoed across the digital landscape. It pulled back the curtain on a chilling reality: in the world of social media, our digital lives are more vulnerable than we ever imagined.
Why Your Social Media Privacy is Your Most Valuable Asset in the Digital Age
Identity Theft: The Silent Epidemic of the Digital Era

Protect Your Identity: Safeguard Your Social Media Privacy to Prevent Identity Theft and Secure Your Online Presence.
Imagine waking up to find someone else living your life online. It's not science fiction—it's a daily reality for thousands of victims of identity theft. Without proper privacy measures, cybercriminals can piece together your digital breadcrumbs—a birthday here, a pet's name there—to create a frighteningly accurate replica of your identity.
The consequences go far beyond a few unauthorized purchases:
Financial Ruin: Fraudulent loans drain bank accounts and destroy credit scores.
Legal Nightmares: Imagine being held accountable for crimes committed in your name.
Reputational Damage: In the digital age, your reputation can be shattered with a few keystrokes.
For professionals and businesses, the stakes are even higher. A compromised identity can lead to losing clients, partnerships, and years of hard-earned trust.
The Invisible Stalker: When Location Data Becomes a Weapon
That innocent check-in at your favorite coffee shop? It could be a beacon for those with nefarious intentions. In the wrong hands, location data isn't just invasive—it's a tool for stalking, harassment, and even physical harm.
This risk is amplified for high-profile individuals or those in sensitive positions. Executives, politicians, and public figures must be particularly vigilant, as their movements can be tracked, predicted, and exploited by competitors, activists, or worse.
Cyberbullying and Harassment: The Dark Side of Connectivity
In the Wild West of social media, even adults aren't safe from digital predators. A single misstep, a controversial opinion, or even just being in the public eye can unleash a torrent of harassment that spills from the digital realm into real life.
For businesses and brands, this can translate to coordinated attacks, review bombing, and reputation management nightmares that can take years to recover from.
Your Privacy Toolkit: Building an Impenetrable Digital Fortress
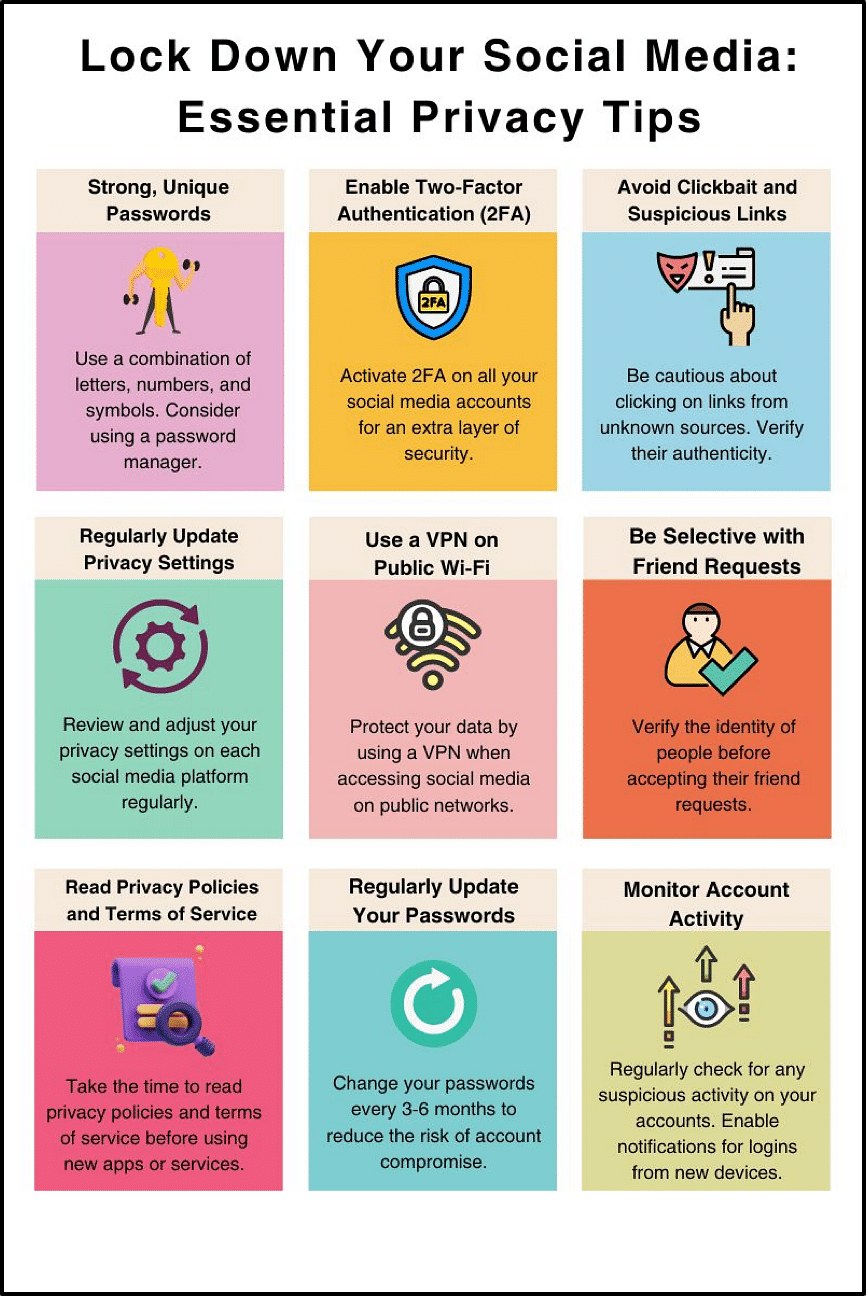
1. Passwords: The Foundation of Your Digital Security
Think of your password as the key to your digital kingdom. In a world where data breaches are announced with alarming regularity, using strong, unique passwords for each account is no longer optional—it's essential.
Use a Password Manager: Tools like LastPass, 1Password, or Dashlane can generate and store complex passwords, so you don't have to remember them.
Length Over Complexity: Aim for passphrases of at least 16 characters. "ILovePizzaWithExtraCheese!" is both memorable and secure.
Regular Updates: Change your passwords every 3-6 months, especially for critical accounts.
2. Two-Factor Authentication: Your Digital Bouncer on Steroids
Imagine having a tough, discerning bouncer at the entrance of your exclusive digital club. That's two-factor authentication (2FA). Even if someone cracks your password, they'll need a second, time-sensitive code to get in.
Use App-Based 2FA: Opt for authenticator apps like Google Authenticator or Authy over SMS-based 2FA, which can be vulnerable to SIM swapping attacks.
Hardware Keys: Consider hardware keys like YubiKey for critical accounts for ultimate security.
3. The Art of Clickbait Dodging: Developing Digital Street Smarts

Beware of Clickbait: Protect Your Social Media Privacy to Avoid Misinformation and Secure Your Online Experience.
In the attention economy, clickbait is the bait, and you're the fish. But these enticing headlines often hide phishing attempts, malware, or scams.
Hover Before You Click: On a desktop, hover over links to see where they really lead.
Use Link Checkers: Tools like VirusTotal can scan suspicious links before you click.
When in Doubt, Don't: If an offer seems too good to be true, it probably is.
4. VPN: Your Invisibility Cloak in the Digital Realm
Browsing without a VPN is like shouting your private conversations in a quiet, crowded room. A VPN encrypts your internet traffic, keeping your online activities private from ISPs, hackers, and nosy networks.
Choose Wisely: Not all VPNs are created equal. Look for providers with a no-log policy and a track record of protecting user privacy.
Always On: Make it a habit to connect to your VPN before you start browsing, especially on public Wi-Fi.
5. Privacy Settings: Fine-Tuning Your Digital Presence
Each social media platform offers a range of privacy settings. Take the time to go through them meticulously:
Facebook: Use the Privacy Checkup tool to review who can see your posts, how people can find you, and what data is shared with apps.
Instagram: Consider setting your account to private and regularly review your list of followers.
LinkedIn: Adjust your public profile settings and control who can see your connections.
Twitter: Decide whether to protect your tweets and who can tag you in photos.
The Unsung Heroes: Social Media Managers as Privacy Guardians
In this digital age, social media managers have evolved from mere content creators to the guardians of digital galaxies. Their role in maintaining privacy and security is more crucial than ever.
The Juggling Act: Managing Multiple Accounts Securely
Imagine being responsible for not just one but multiple digital identities. Social media managers are like skilled circus performers, keeping numerous plates spinning in the air. One slip is not just a plate that crashes—it's potentially thousands of users' data.
Key Responsibilities:
Implementing robust password policies across all accounts
Ensuring 2FA is activated on every platform
Regular security audits of connected apps and third-party tools
The Art of Responsible Sharing
In a world hungry for content, social media managers must be both creators and gatekeepers. They're the last line of defense, ensuring that in the rush to engage and entertain, they don't accidentally give away sensitive information.
Best Practices:
Develop clear guidelines on what can and cannot be shared
Implement a multi-step approval process for sensitive content
Stay updated on privacy laws and platform-specific regulations
The Tech Wizards: Mastering Security Tools
Social media managers are the tech-savvy wizards of the digital realm. Armed with an arsenal of security apps and tools, they constantly update, patch, and fortify the digital walls that keep barbarians at bay.
Essential Tools:
Social media management platforms with robust security features
Analytics tools that respect user privacy
Crisis management software for quick response to potential breaches
Your Call to Action: Become the Hero of Your Digital Story
The digital world can be a scary place, but armed with knowledge and the right tools, you can transform from a potential victim to the hero of your own digital narrative. Here's your mission, should you choose to accept it:
Conduct a thorough audit of your current social media privacy settings. Are they Fort Knox or a paper fortress?
Implement a password manager and two-factor authentication across all your accounts. No exceptions.
Develop a keen eye for digital traps. Train yourself and your team to spot phishing attempts and suspicious links.
Invest in a reputable VPN service and make it a habit to use it, especially when on public networks.
Create a personal or company-wide social media policy that prioritizes privacy and security.
Stay informed about the latest privacy threats and countermeasures. The digital landscape is constantly evolving.
Educate your friends, family, or employees about the importance of social media privacy. Be the privacy superhero your circle needs.
Remember, in the digital age, your privacy is not just a right—it's your power and your responsibility. Guard it carefully, wield it wisely, and never underestimate its importance. The fate of your digital kingdom rests in your hands. Are you ready to rule it with the vigilance it deserves?
In a world where data is the new oil, your privacy is the fortified vault that keeps it safe. By implementing these strategies and maintaining constant vigilance, you're not just protecting yourself—you're setting a standard for digital citizenship in the 21st century. The question isn't whether you can afford to take your social media privacy seriously; it's whether you can afford not to.
Before you go, here's a practical and easy-to-use printable poster to help you protect your social media accounts,